Sealed Secrets
This guide will explore Kubernetes secrets, with a specific focus on sealed secrets.
In this guide, we will demonstrate the steps required to encrypt Kubernetes secrets with sealed secrets in Runme successfully.
Prerequisites
To get started, ensure you have the following:
Clone the repository
We created a notebook repository containing all the instructions and commands required for this guide.
git clone https://github.com/stateful/blog-examples.git
cd kubernetes/k8s-secret/sealed-secret
Install Runme
Install the Runme extension on VS Code and set it as your default Markdown viewer.
This guide will focus on using the Mac specifications. If you use a Linux OS, follow the instructions in the Linux Markdown files.
Install all dependencies
To follow up on securing your secrets using Sealed Secrets, ensure you install the necessary dependencies in the notebook's prerequisite section. In your Runme cell, run the commands below to install all dependencies required for this guide.
brew install kind
brew install kubectl
brew install kubeseal
Encrypt a secret in Runme
To encrypt a secret, you must create a Kubernetes secret and then using kubeseal you can encrypt it. Run the command below in your Runme cell to encrypt your secret.
kubectl create secret generic mysecret --from-literal=username=myuser --from-literal=password=mypassword --dry-run=client -o yaml | kubeseal > mysealedsecret.yaml
Or you can encrypt a manifest file mysecret.yaml (containing your secret).
kubeseal < mysecret.yaml > mysealedsecret.yaml
Or you can use the sealed-secrets-controller installed in your cluster to encrypt secret before deploying.
cat mysecret.yaml | kubeseal --controller-namespace kube-system --controller-name sealed-secrets-controller --format yaml > mysealedsecret.yaml
For all of the above, Runme will automatically create a sealed secret resource containing the encrypted data, the mysealedsecret.yaml
Adding a new value to a secret
To add a new value to a secret, you only need to update your manifest file with the new values, re-encrypt the secrets, and then reapply them to the cluster. All of these can be executed in your Runme cell. To do this, run the command below
kubeseal --controller-namespace=kube-system --controller-name=sealed-secrets-controller < new_secret.yaml > mysealedsecret.yaml
kubectl apply -f mysealedsecret.yaml
Here's what it looks like when the command is executed in Runme.
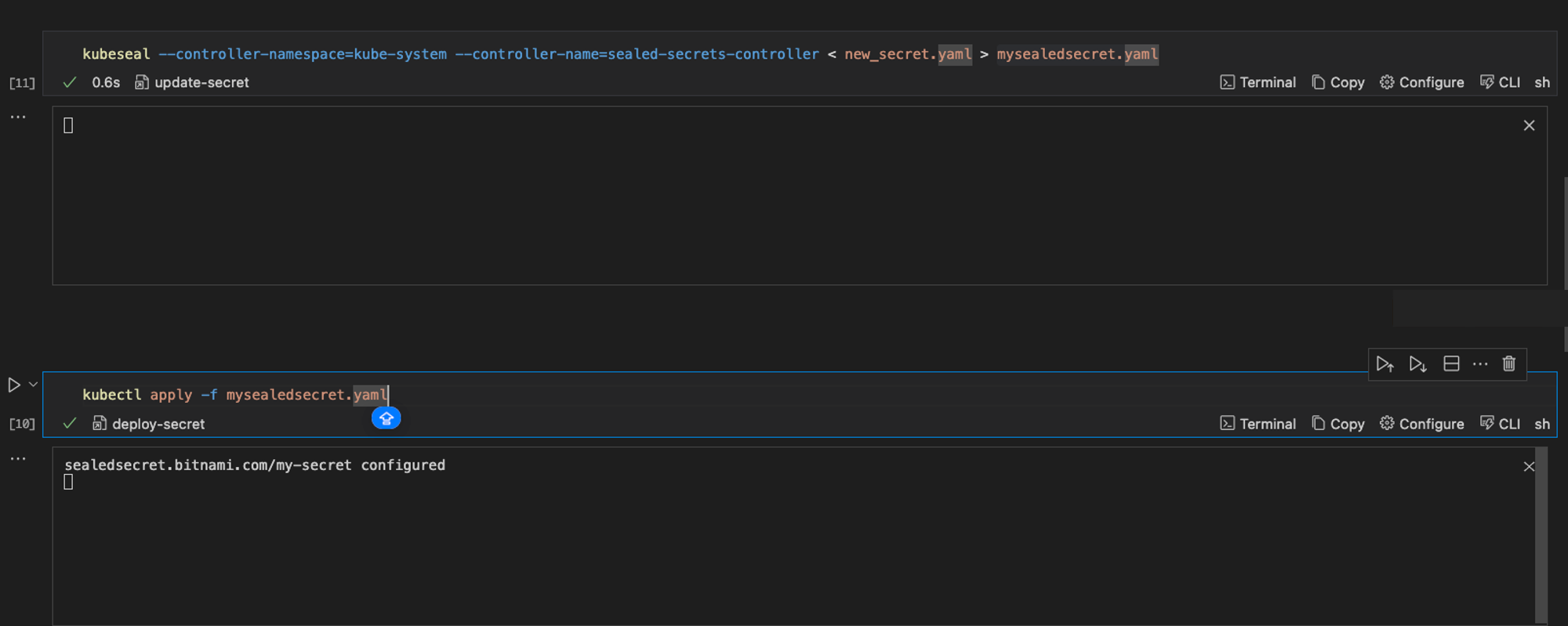
From the output you can see that your new value has successfully been added.
Decrypt a secret
To retrieve the original version of runme-secrets.yaml, you can decrypt the encrypted secret, mysealedsecret.yaml. Run the command below
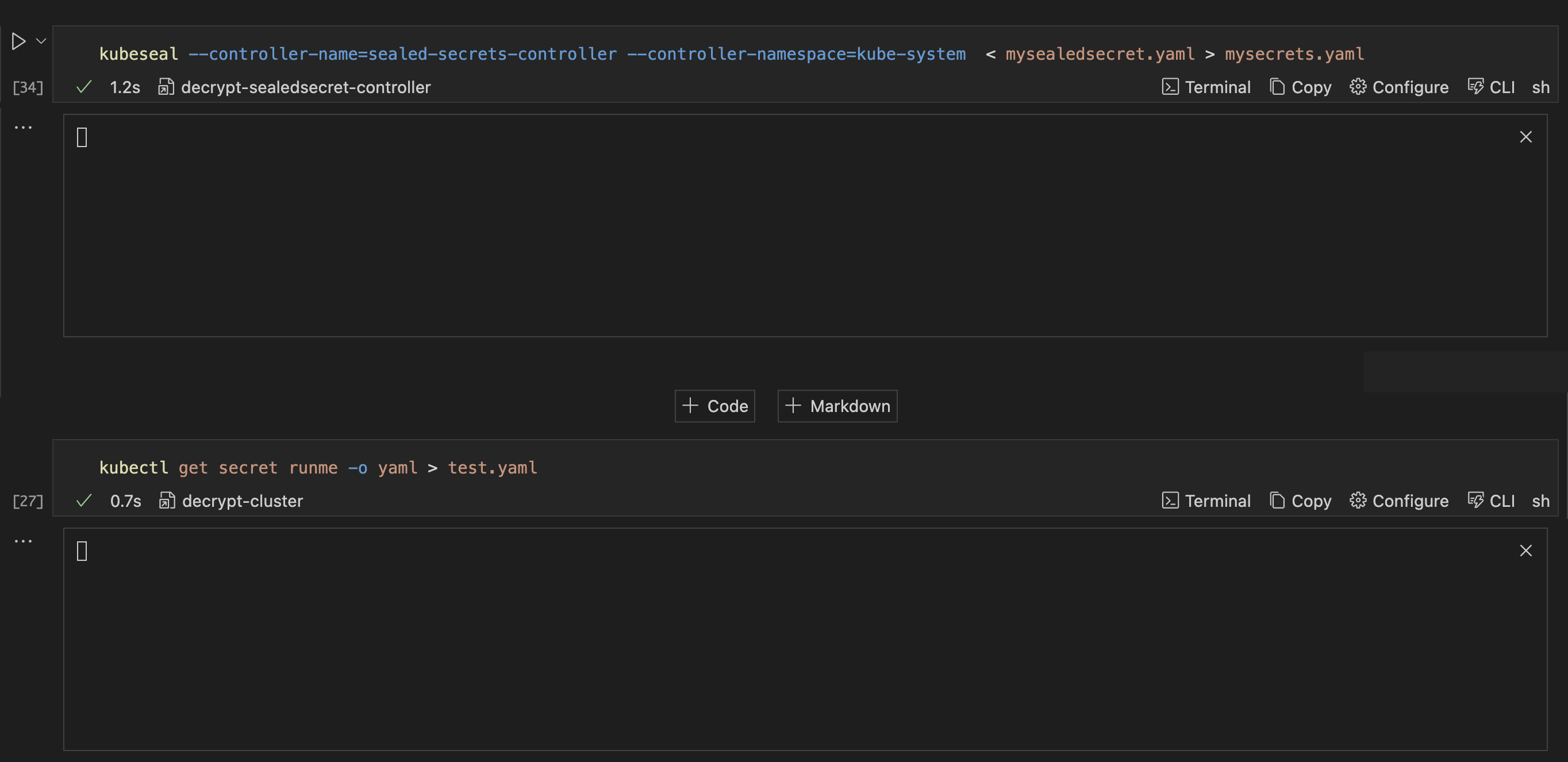
kubeseal --controller-name=sealed-secrets-controller --controller-namespace=kube-system < mysealedsecret.yaml > mysecrets.yaml
When you run the code in your Runme cell, here is what it looks like.
Delete a secret
kubectl delete -f mysealedsecret.yaml
Deploy the sealed secret
kubectl apply -f mysealedsecret.yaml
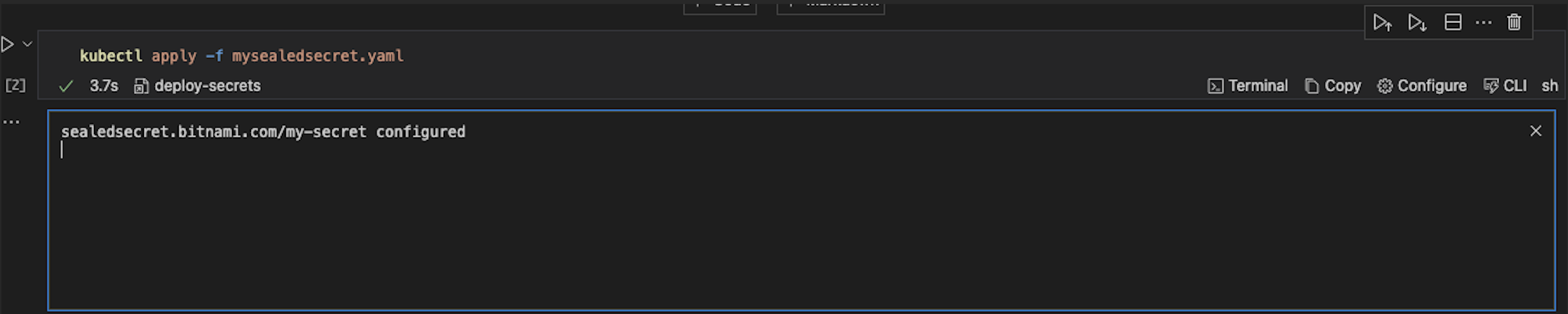
The Sealed Secrets controller will decrypt the Sealed Secret and create a Kubernetes Secret with the decrypted data.
Make sure to replace placeholders like mysecret.yaml and mysealedsecret.yaml with your secret and Sealed Secret filenames. Adjust controller-specific details such as the namespace and name according to your environment.